Task hijacking
Introduction
Task hijacking is a vulnerability that affects Android applications due to the configuration of Task Control features in the AndroidManifest.xml file. This flaw can allow an attacker or a malicious app to take over legitimate apps, potentially leading to information theft.
Scenario
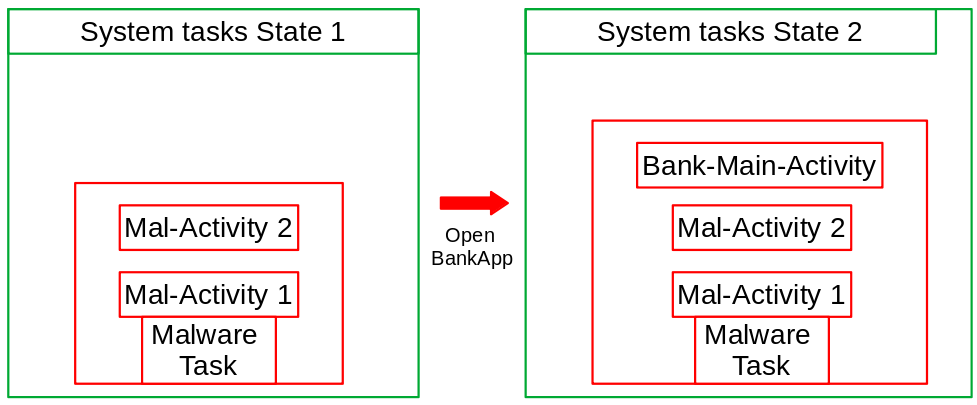
Security implication (this scenario)
When the back button is pressed on Bank-Main-Activity, the user will go to the Mal-Activity 2.
Note
Requirements:
- The app can be installed on Android SDK version < 28 (Android 9). Check
android:minSdkVersionis < 28 inAndroidManifest.xml- This vulnerability is patched from Android SDK version 28. [↗]
android:launchMode="singleTask"inAndroidManifest.xml(necessary for this scenario)
Testing
You can use malware apk by ivan sincek.
To hijack a task, modify the task affinity in AndroidManifest.xml of malware.apk under MainActivity. Set it to PackageNameVictim and rebuild the APK.
Example:
<! -- AndroidManifest.xml victim.apk -->
<manifest ... package="com.victim.bank" ...>
<! -- AndroidManifest.xml malware.apk -->
<activity android:name="com.kira.malware.activities.MainActivity" android:exported="true" android:taskAffinity="com.victim.bank" ...>